How Impinj Cryptography Expert Matthew Robshaw Safeguards RAIN RFID
The Impinj technical fellow shares how his rich knowledge of cryptography and RAIN RFID has helped shape standards and solutions for authenticity and brand protection.
Matthew Robshaw may not see himself as a security guard, but the technology he’s developing at Impinj helps protect manufacturers, retailers, and consumers from some of the costliest, most trust-eroding crimes out there.
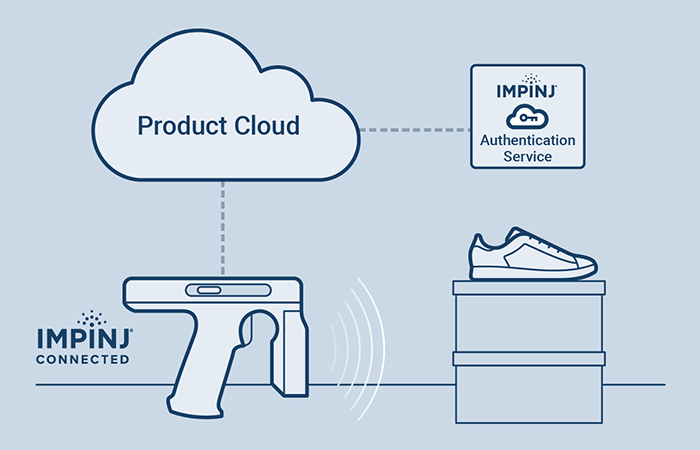
As an Impinj technical fellow and expert in cryptography, Matt is a pivotal contributor to the Impinj Authenticity™ solution engine — a product authentication and brand protection offering that uses a combination of RAIN RFID tags, readers, and cloud services to identify counterfeit and gray-market goods before they make it into the hands of unsuspecting consumers.
Matt earned his Ph.D. at the University of London and has spent his career working on the development and deployment of cryptography, first at RSA Laboratories in the United States and later at France Télécom/Orange in Europe. He’s been with Impinj since 2012.
I’ve had the pleasure of working with Matt throughout his time at Impinj. His enthusiasm for his work is inspiring, and I greatly appreciate his ability to make the most complex topics easily accessible to a non-technical audience. He, like many others at Impinj, has an established track record of innovation and a thirst for problem-solving.
Recently, I spoke with Matt, who shared more about his background, international RAIN standards, and how he envisions item authentication becoming a ubiquitous part of RAIN deployments.
Q: Your title is “technical fellow” — can you explain what that means and what your job entails?
A: I am one of several technical fellows at Impinj. It is perhaps an unusual title, but it helps to identify colleagues with a deep and focused expertise. While a technical fellow might be an expert in one area, they will likely contribute to several projects and work with multiple teams across the organization. My focus is on cryptographic design and architecture, which is concerned with integrating algorithms and any supporting infrastructure into RAIN RFID tags, readers, and solutions.
Q: How did you get introduced to RFID?
A: My research has always been focused on the design and deployment of cryptography. During the 2000s, an interesting challenge cropped up. Just as some wonderful new algorithms and protocols were ready for widespread use, we were seeing the first substantial stirrings of the Internet of Things. It was soon realized that security features we take for granted on a PC or laptop would never fit into the cutting-edge miniature devices that were in development. Thus, the field of cryptography for very constrained environments was born, with the greatest challenge being posed by tiny RAIN RFID tag chips.

Q: You’ve been deeply involved in the development of global RAIN RFID operating standards. What’s the latest?
A: I’ve had the good fortune to work in many research and standardization groups over the years. In the early years, I worked with industry and academic colleagues on several European research projects that were devoted to exploring security for RAIN RFID. The most promising technologies from those efforts were then incorporated into international ISO/IEC standards. Throughout this multi-year process, the collective goal was to ensure that the industry would have the necessary standards in place for large-scale deployments of cryptographic RAIN RFID chips.
The timing turned out well, but our work continues. Standards development can be slow, and it can take three to four years to get a new work item to publication. The forthcoming GS1 EPC Gen2v3 standard may lead to more efficient implementations in the field. Unsurprisingly, we’re keen to start work on any accompanying ISO/IEC standards that will help pass on these improvements to the end user.
Q: Why did you join Impinj?
A: One of the things that drew me to Impinj was a shared view of what an authentication solution could look like. A complete authentication solution has many parts, from the tag chip implementation and reader support, through the important issue of key management, and on to international standardization. Without this bigger picture, the risk of a false start is considerable. It was that understanding of the full ecosystem that was appealing to me. Right from the get-go, it was understood we would be providing all the parts of what came to be called the Impinj Authenticity solution engine.
[ Want to read more content like this? Subscribe to the Impinj blog. ]
Q: How would you describe the value of Impinj Authenticity, the solution engine that protects items from counterfeiting?
A: In any security deployment, you need to establish a point of trust. By providing each Impinj M775 tag chip with a unique cryptographic key, we have provided a foundation on which trust can be built. This might seem abstract, but it is the foundation of Impinj Authenticity. At the same time, we didn’t want Impinj Authenticity to be difficult for our partners and end customers to use. One of the most difficult steps in deploying cryptography is “key management” — generating keys and getting them to where they need to be. The value of Impinj Authenticity is that we take care of that problem and we provide a complete infrastructure for our partners to build on.
Q: Establishing and maintaining trust and security is at the heart of what you do. What goes into creating a workable brand-protection solution that instills confidence?
A: Any security solution takes a significant amount of up-front effort. There will always be bad actors, so it’s important to identify their motives and understand their resources when they try to compromise a system. Different applications and solutions will present different cost-benefit balances to the attacker. The goal is to drive up the attacker’s costs while driving down the benefits to a point where they’ll spend their time somewhere else.
Obviously, there is a corresponding cost-benefit analysis on the design side, too, so a viable brand-protection solution requires finding the appropriate balance. I think Impinj has found a good balance: a secure brand authentication solution that’s easy to deploy at scale without compromising the tag and reader performance we’ve come to expect from RAIN RFID.
Learn more about RAIN RFID product authentication – how it works, how it helps fight counterfeits, and how it compares to traditional methods for verifying item authenticity.
- Article tagged as:
Tuesday, November 21, 2023
ABOUT THE AUTHOR

Jill West
Vice President, Strategic Communications
Jill West leads Impinj IoT technology adoption marketing initiatives across numerous markets including retail, healthcare, and supply chain and logistics.
Sign Up for the latest news
